Hi Cloud Marathoners!
Welcome to the new blog post (Part 4/12) from the Az-305 series to help you get ready for the AZ-305 exam.
Please, check the previous post(s) listed below, if you landed on this page for the first time 🙂
Table of content (blog series)
- *** Design Identity, Governance, and Monitoring Solutions ***
- Part 1: Design a governance solution
- Part 2: Design Authentication and Authorization Solutions
- Part 3: Design a solution to log and monitor Azure resources
- *** Design Infrastructure Solutions ***
- Part 4: Design a compute solution
- Part 5: Design an application architecture solution
- Part 6: Design a network infrastructure solution
- Part 7: Design a migration solution
- *** Design Data Storage Solutions ****
- Part 8: Design a non-relational data storage solution
- Part 9: Design a data storage solution for relational data
- Part 10: Design a data integration solution
- *** Design Business Continuity Solutions ***
- Part 11: Design a solution for Business Continuity, backup and disaster recovery
- Part 12: Design for high availability
What is the Compute service in Cloud?
The keyword “compute” refers to the hosting model for the computing resources that your application runs on. However, “cloud computing” is the on-demand availability of computer system resources, like a data storage and computing power without direct active management by the end user.
The compute services play very important role in delivery of digital services and
defining a purposeful compute solution for your project is the first critical step 😎

WHAT YOU CAN DO WITH compute services in azure?
The Azure “Compute” provides the infrastructure you need to run your application, whether you’re building from scratch or deploying existing ones. You could easily pick a compute capacity in the cloud and scale on demand. A variety of services allow you to containerize your applications, deploy any OS in virtual machines (VMs), and take advantage of flexible options to plan and execute your VMs migration into Azure.
You can also rely on comprehensive support for hybrid environment solutions by deploying where you want to. The Azure compute services are supported with enterprise grade integration solutions including identity solution. By using Azure cloud platform you can manage end-point protection, and Active Directory support that helps secure access to on-premises and cloud workloads and applications.
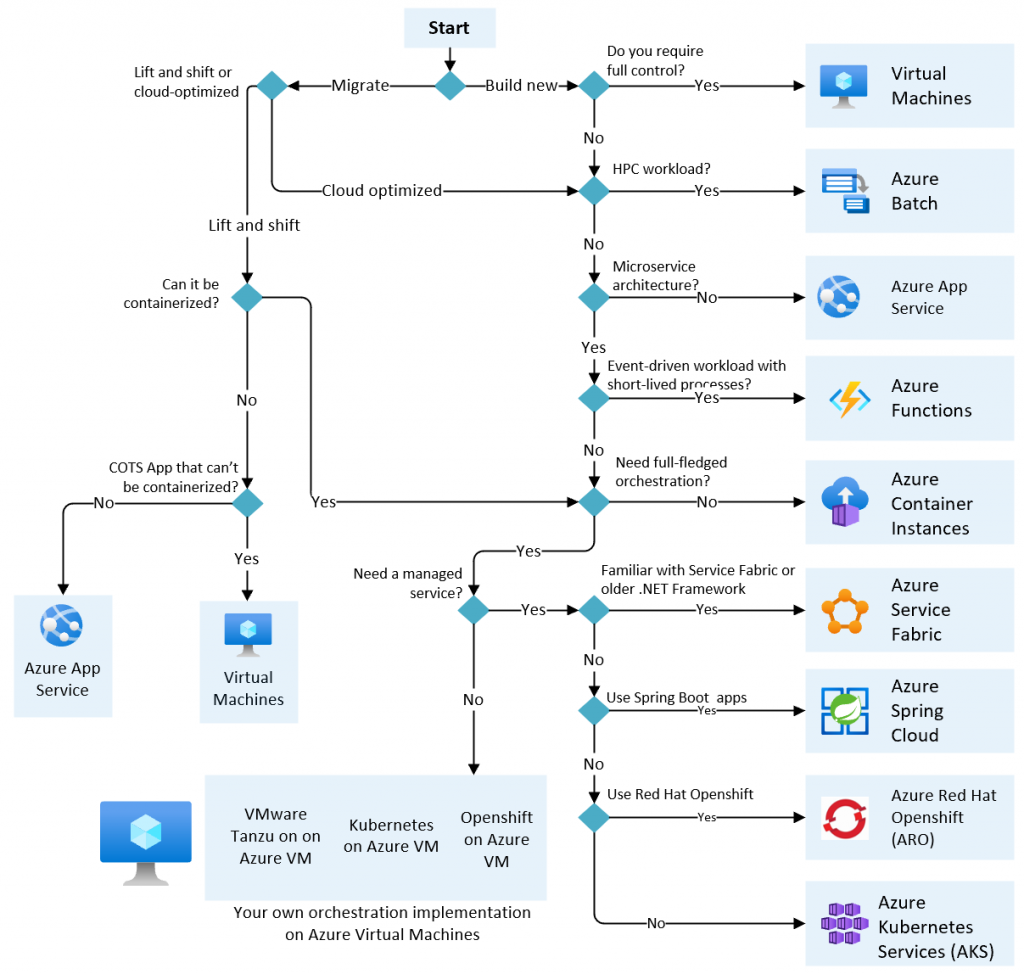
Part 4: Design a compute solution
The references below are taken from official Microsoft docs and focused on designing compute solutions in Azure. You could also find it helpful to check the Microsoft docs and learning paths with [Tutorials] below 😉.
This collection of links are gathered with a focus toward the exam objectives of AZ-305 certification exam.
Shared responsibility in the cloud
Choose an Azure compute service for your application
Sizes for virtual machines in Azure
Azure Batch best practices
Azure Marketplace – Compute
Azure App Service plan overview
App Service overview
Set up staging environments in Azure App Service
What is Azure Container Instances?
What is Kubernetes?
Azure Kubernetes Service (AKS)
CUSTOMER CASE STUDY – Azure Functions (Serverless Computing)
CUSTOMER CASE STUDY – Azure Logic Apps and Azure API Management
Security considerations for Azure Container Instances
Getting started with Docker
Run background tasks with WebJobs in Azure App Service
Azure Logic Apps
What is Azure Batch?
Linux Virtual Machine Pricing
Choose the best Azure service to automate your business processes
Integration Services
Authentication and authorization in Azure App Service and Azure Functions
[Tutorial] Create an Azure Batch account by using the Azure portal
[Tutorial] Host a web application with Azure App Service
[Tutorial] Introduction to Azure Logic Apps
[Tutorial] Introduction to Azure virtual machines
SUMMARY
Thank you for visiting the AZ-305 Study Guide and checking the Part 4 – Design a Compute solution on Azure.
The next blog post will cover the Part 5: Design an application architecture solution.