Hello dear friends,
I would like to welcome everyone who is landed on this page to check out the Azure Spring Clean 2023 event and Learn new cloud skills!
Before kicking off the topic, I would like to start with a “THANK YOU” message for the organizers of the event; especially for Joe, Thomas, and everyone who is involved in making this event a successful experience for everyone!
Note:
Introduction
In the spirit of Azure Spring Clean, we will explore how to organize Azure Security Services using the infrastructure-as-Code (IaC) approach with Azure Bicep.

We will look into how you could declaratively define and deploy your Azure security resources including Azure Policies to tackle real-world business problems. So, get yourself ready for simple yet powerful demos that will turn you into a hero.
And don’t worry, if you are new to Azure Bicep as we will have a super express introduction to this new IaC language to get you started with fundamentals.
By the way, if you are super new to Azure Bicep then please check the following YT recording – “What is new in Azure Bicep language?”
What is Azure Bicep
Azure Bicep is a new declarative Domain Specific Language (DSL) for provisioning Azure resources. The purpose of Azure Bicep is to simplify the resource creation and management experience with a cleaner syntax and more code reuse.
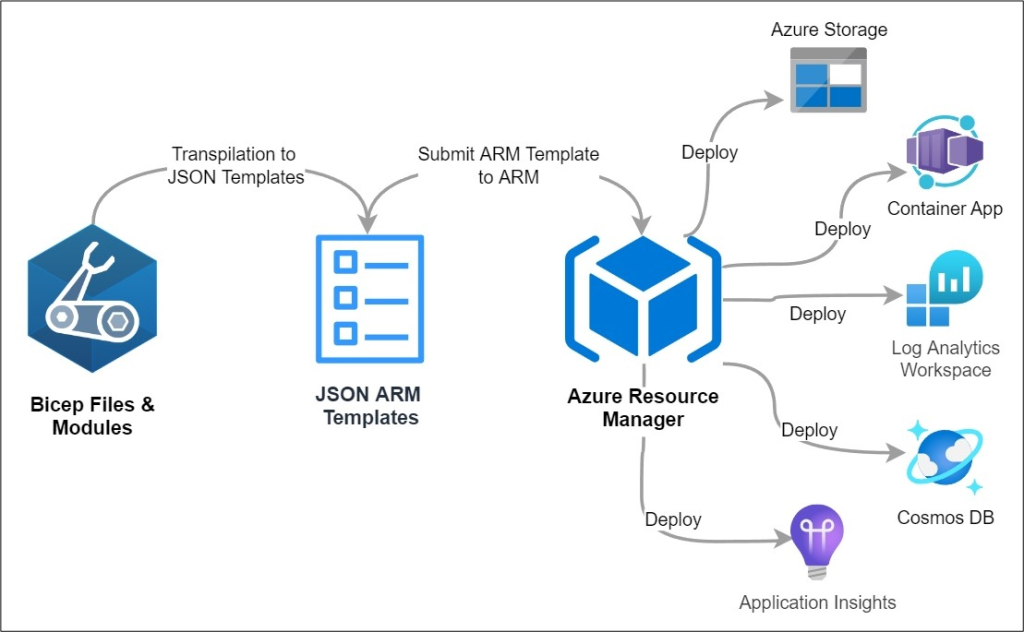
Declaring resources as IaC
There are many benefits in declaring and managing cloud infrastructure resources as a code. It provides benefits, such as increased compliance, visibility, controlled deployments and versioning of changes that get deployed into your cloud environments.
The following screenshot demonstrates how Azure Bicep declares cloud resources on the left side of the panel:
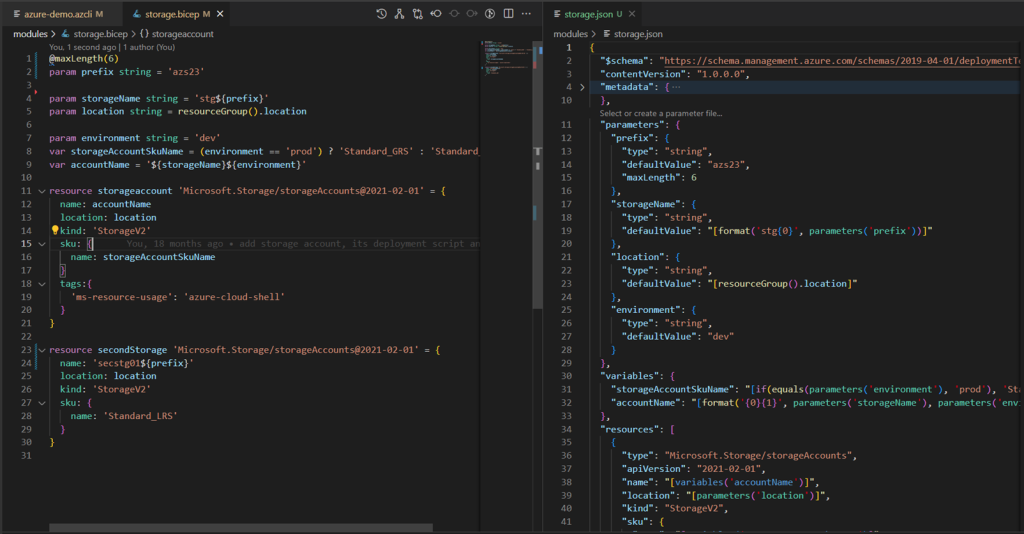
Organizing cloud resources
No matter how small or big is your project, taking time to think through the approach of how to organize your digital assets is an important task. In Microsoft Azure, you would need to consider a couple of points while trying to make this decision. Namely, you would need to consider the following factors:
- Resource Governance approach
- Management scopes
- IaC management options
- Modules, ACR, Template Specs, etc.
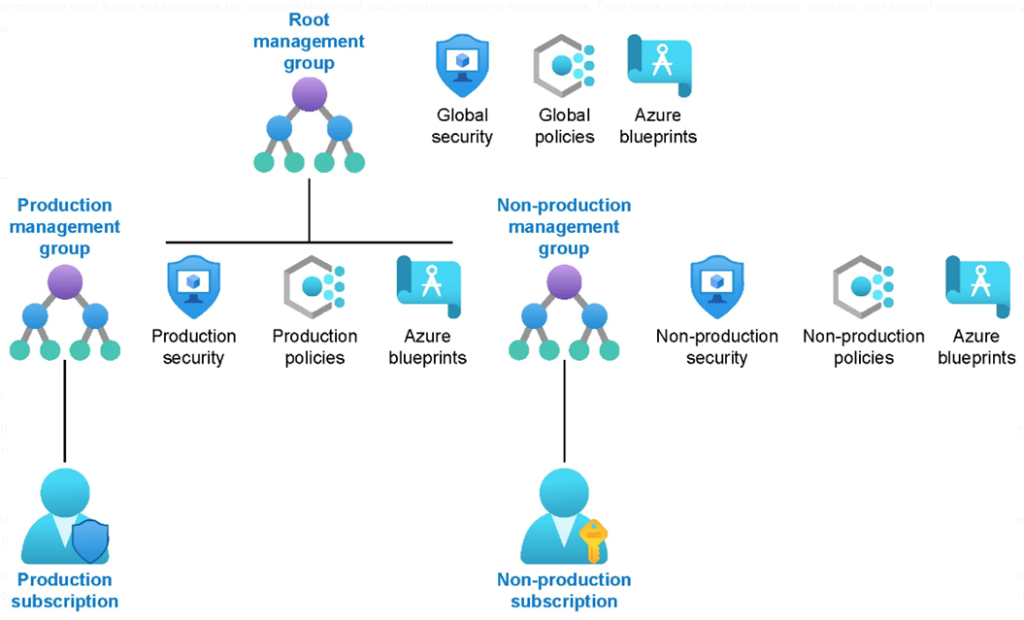
Azure Policies for governance
The Azure Policies are assigned with a unique mission to guard the compliance aspect of your cloud resources and workloads. It evaluates resources at specific times (by default happens every 24 hours) during the resource lifecycle changes and the policy assignment lifecycle updates.
Thus, whenever you get a resource created, updated, or deleted within a scope of the monitored compliance, or if you update/create an Azure policy then the compliance evaluation cycle will determine the compliance of these changes by auditing, blocking, or allowing the action to be performed.
Securing storage account options
Note: this section of the post is in progress…
It will be presented with the screenshots and GitHub repo for you.
Stay tuned, and check in a few days 😉
video & Demo – a sweet combo
In the video below, I briefly cover the posted information in this blog post which also includes the instructions on how to run the demo and get the scripts to deploy Azure Policies for your Tag Governance scenario.
Without any overdue, here is the video that should be available to you:
The following image is a screenshot from the slide that demonstrates the Bicep code that declares the policy definition and initiative, with the final view of deployment on the Azure portal.
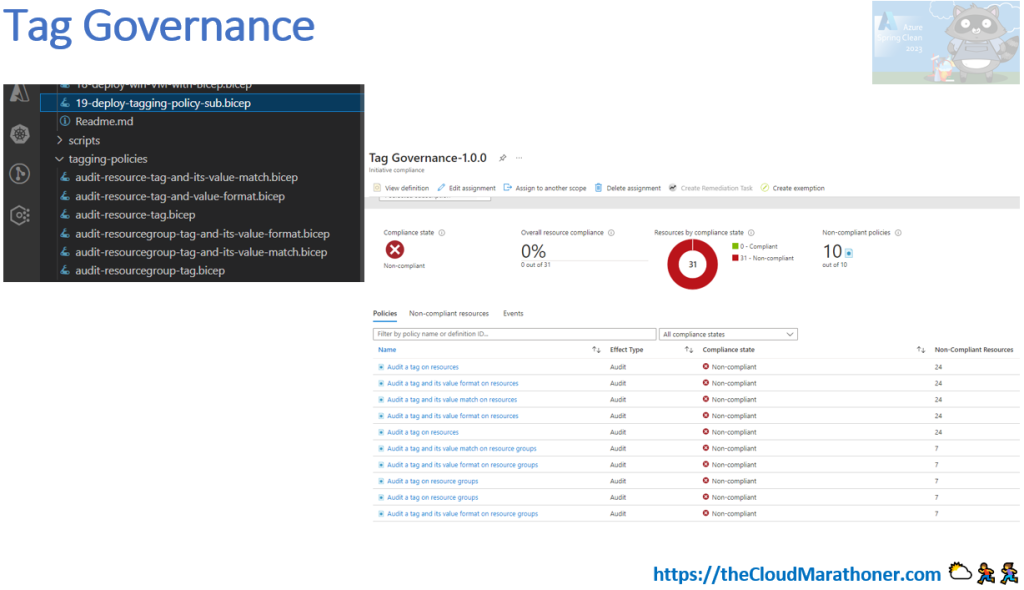
Please, feel free to check out the GitHub repo – Learn Azure Bicep.
Summary
Thank you so much for reading this post and learning about Azure security and compliance and how IaC language Azure Bicep can help you in this journey. This is a bit different perspective to strengthen your resource/workload compliance on Azure using IaC approach.
Please, keep up the good work by securing your organizational and customer cloud environments!
![]()
