Hi, my dear #CloudMarathoner friends!
So, how you could apply Zero Trust (ZT) principles to a virtual network in Azure 🚀 infrastructure ⁉️ 🤔
Securing your infrastructure with ZT principles
🔒 Securing Your Infrastructure with Zero Trust Principles 🔒
In today’s landscape of sophisticated cyber-attacks and data breaches, ensuring the security of your infrastructure is paramount. Implementing a robust security framework is essential to protect your organization’s assets.
One highly recommended approach is adopting Zero Trust principles. This framework operates under the mantra of “never trust, always verify,” meaning no user or device is automatically trusted, and all requests are verified before access is granted.
What are the benefits of ZT?
The benefits of Zero Trust are very critical in modern security landscape where your customer workloads are running or planned to be migrated to. Thus, let’s identify them with the following three main characteristics:
✅ Enhanced Security: Multiple layers of verification and authentication protect your infrastructure from potential threats.
✅ Complete Visibility: Monitor and track all access requests and transactions in real time to identify potential threats.
✅ Regulatory Compliance: Ensure adherence to industry regulations like GDPR, HIPAA, and PCI-DSS.
What are the challenges in ZT?
There are always challenges with the new change or framework, especially in established organizations. Thus, expect resistance to the changes and work with the stakeholders of the organization and program to overcome these high-level challenges below:
✅ Starting Point: It can be overwhelming to secure everything at once.
✅ Access Management: Adopting a least-privilege access approach requires careful management of identity and access policies.
✅ Up-to-date Security: Ensuring all components, from OS to cloud services, are secure and current.
Are there best practices for implementation?
Yes, of course we will share those points with you. Based on a number of feedbacks from reputable organizations. here is the summarized version of expected challenges in your way.
1️⃣ Create a Clear Roadmap: Define goals and timelines for implementing Zero Trust principles.
2️⃣ Build a Comprehensive Strategy: Regularly assess infrastructure, continuously monitor for threats, and establish rapid incident response processes.
3️⃣ Phased Approach: Break down the implementation process into manageable steps, prioritizing critical areas first.
4️⃣ Leverage Azure Tools: Utilize Azure Active Directory, Azure Sentinel, and Azure Policy to automate security tasks and gain real-time visibility.
5️⃣ Invest in Training: Ensure your team has the necessary skills and knowledge to implement Zero Trust effectively.
Practical application of ZT in Azure VNet
There is a good reference to architectural diagram on Microsoft Learn documentation. You could use the Use the following diagram as a starting point to secure access to the VNet and applications in your Azure environment.
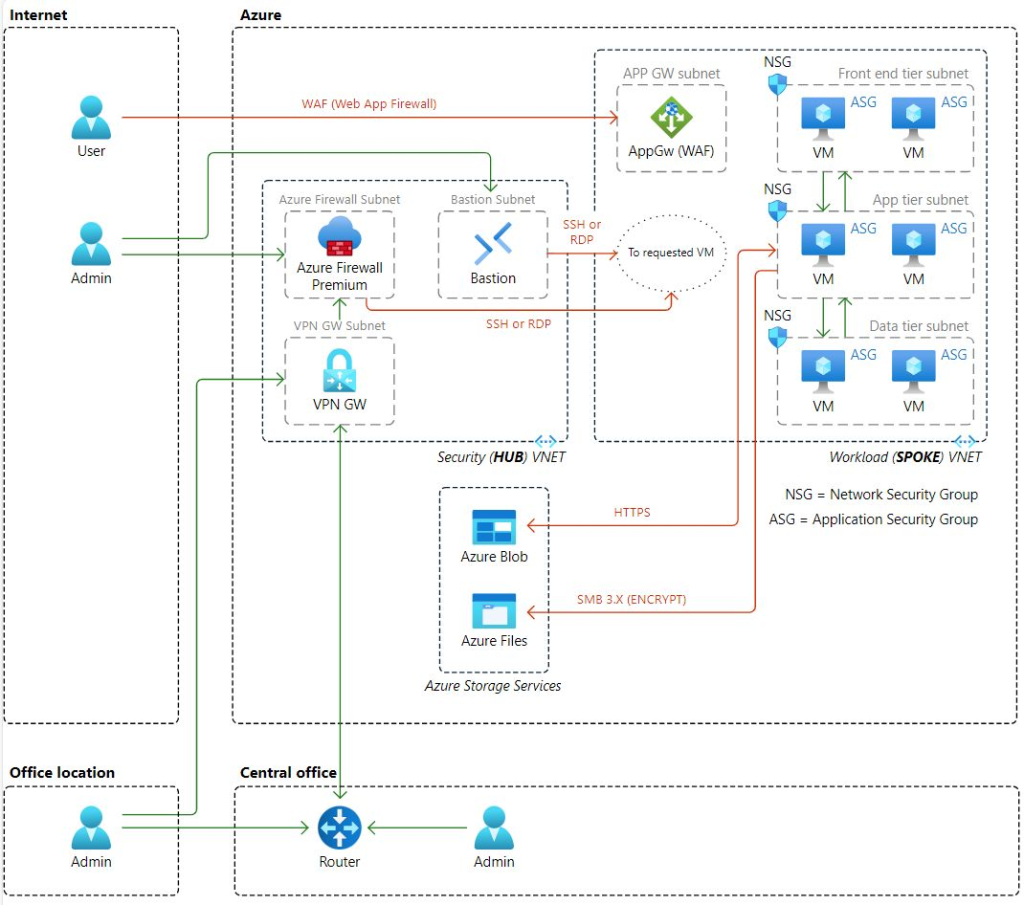
This reference architecture includes two main parts:
🥇 Securing traffic within the Azure environment to the application.
🥈 Using multifactor authentication and conditional access policies for user access to the application.
[Credit 🖐] Apply Zero Trust principles to a spoke virtual network in Azure
at Microsoft Learn docs 👉 https://lnkd.in/ei-rWUhc
Call to action
Please, let me know your feedback and challenges with ZT principals, and specifically the security controls you are applying or planning to apply into your networking environment.
You are always welcome to check my LinkedIn post and provide your valuable feedback 👉 https://www.linkedin.com/posts/elkhanyusubov_cloudarchitecture-azure-sharingiscaring-activity-7280953566599557123-ZnmD


