Hello Cloud Marathoners,
I have been asked to expand upon set of available Microsoft Azure services that could help with compromised user devices. One way to deal with such scenarios is to temporarily suspend user access until endpoint is cleaned.
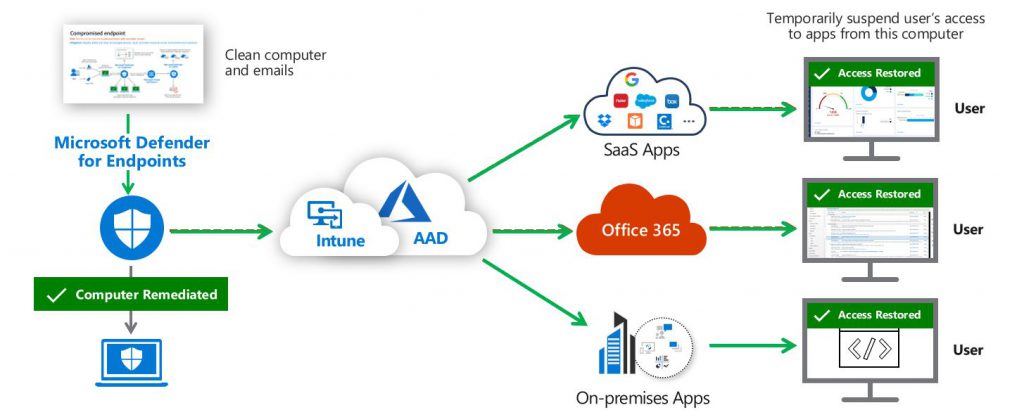
Taking into account that your user’s device is compromized, you can automate response either to restric or restore the access to the endpoint.
Option#1 – Retrict Access
To help with this scenarious you could use the Azure AD’s Conditional Access features. The Conditional Access knows about the device risks because Microsoft Defender for Endpoint (MDE) notified Intune, who then updated the compliance status of the device in Azure AD.
During this period, the user is restricted from accessing corporate resources. These applies to all new resource requests and will block any current access to resources that support continuous access evaluation (CAE).
Your user will still be able to do general internet productivity and research (like Wikipedia, external web resources and anything else that doesn’t require corporate authentication), but won’t have access to corporate resources.
Option#2 – Restore Access
The second option (illustrated on infographic) mitigates the “Access restored” scenariou. This correspondce to sceanriou wher threat has been remediated and cleaned up, MDE triggers Intune to update Azure AD and Conditional Access restores the user’s access to corporate resources.
Described two scenarious above, mitigate the risk to the organization by ensuring attackers who may be in control of these devices cannot access corporate resources, while minimizing the impact on user productivity to minimize disruption of business processes.
What is next?
Check this interesting references on Microsoft docs and learn about Continue Access Evaluation (CAE) – and other Common Conditional Access policies.
Fᴏʟʟᴏᴡ ᴍᴇ 🎯 ᴀɴᴅ become ᴀ #cloudmarathoner ⛅🏃♂️🏃♀️ – 𝐋𝐄𝐓’𝐒 𝐂𝐎𝐍𝐍𝐄𝐂𝐓 👍#microsoftazure
#conditionalaccess
#compromiseduser
#continuouslearning
![]()
