Greeting to all #CloudMarathoner friends,
Recently, I have been asked more about Azure VNet and some best practices in building a resilient, secure, and scalable network infrastructure in Microsoft Azure platform.
This is a very huge and important topic and will not be addressed with just one post. However, I will try to address this important topic high level recommendations and guidelines that Microsoft recommends, and I followed in my design sessions with the customers.
Where to get started?
Let’s consider the following comprehensive guide that will help you get started.
This is – in no way or shape a completed guidelines and does require improvements over time, based on your custom application, compliance and workload requirements.
1️⃣ Design Your Network Architecture
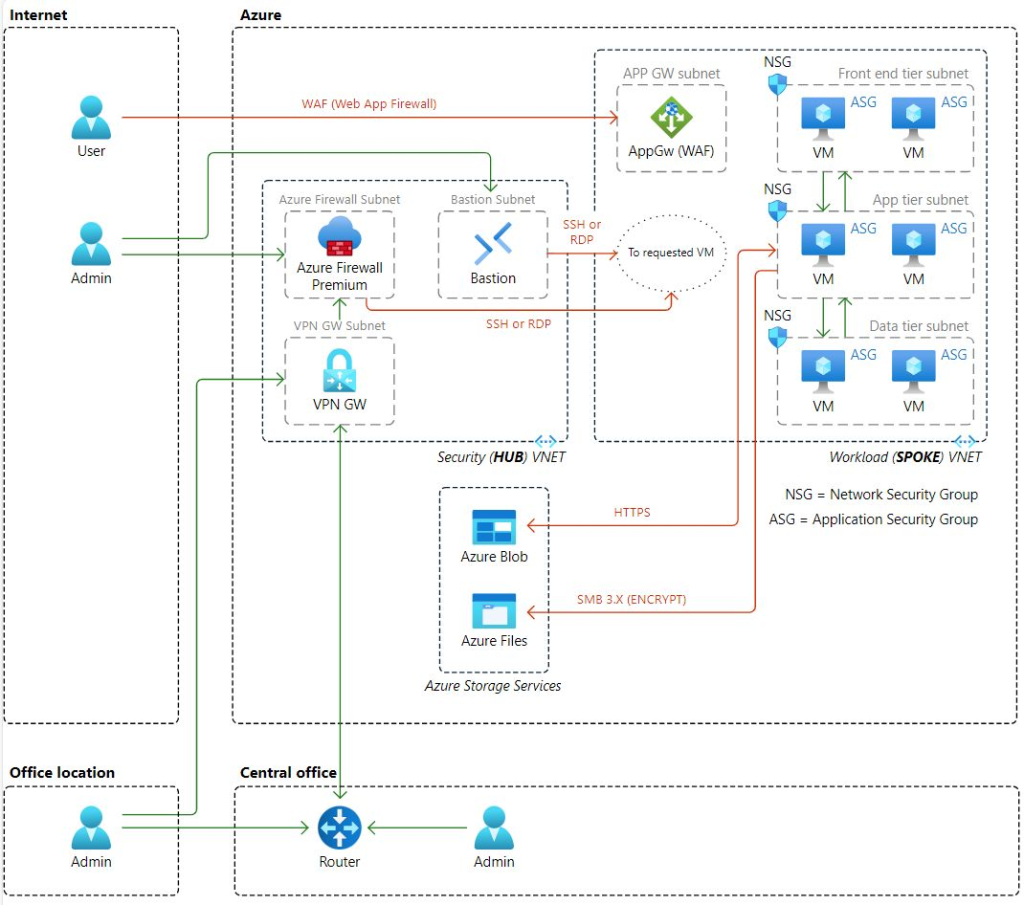
✅ Virtual Networks (VNets): Create VNets to logically isolate your resources. Use subnets to segment the network for better management and security.
✅ Hub-and-Spoke Topology: Implement a hub-and-spoke model to centralize shared services in the hub VNet and connect multiple spoke VNets for isolation and scalability
2️⃣ Implement Network Security
✅ Network Security Groups (NSGs): Use NSGs to control inbound and outbound traffic to your resources. Define rules based on IP addresses, ports, and protocols.
✅ Azure Firewall: Deploy Azure Firewall for centralized network security. It provides threat intelligence-based filtering and logging
✅ Azure DDoS Protection: Enable DDoS protection to safeguard against distributed denial-of-service attacks.
3️⃣ Optimize Performance and Efficiency
✅ Azure Load Balancer: Use load balancers to distribute traffic across multiple resources, ensuring high availability and reliability.
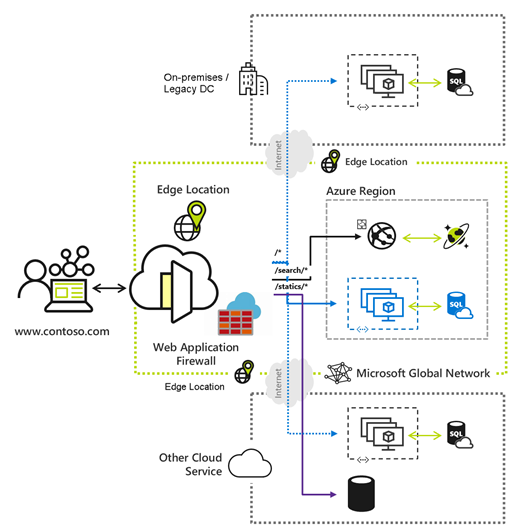
✅ Azure Application Gateway: Implement Application Gateway for web traffic load balancing, SSL termination, and web application firewall capabilities.
✅ ExpressRoute: Establish private connections between your on-premises networks and Azure for faster and more reliable connectivity
4️⃣ Ensure Scalability
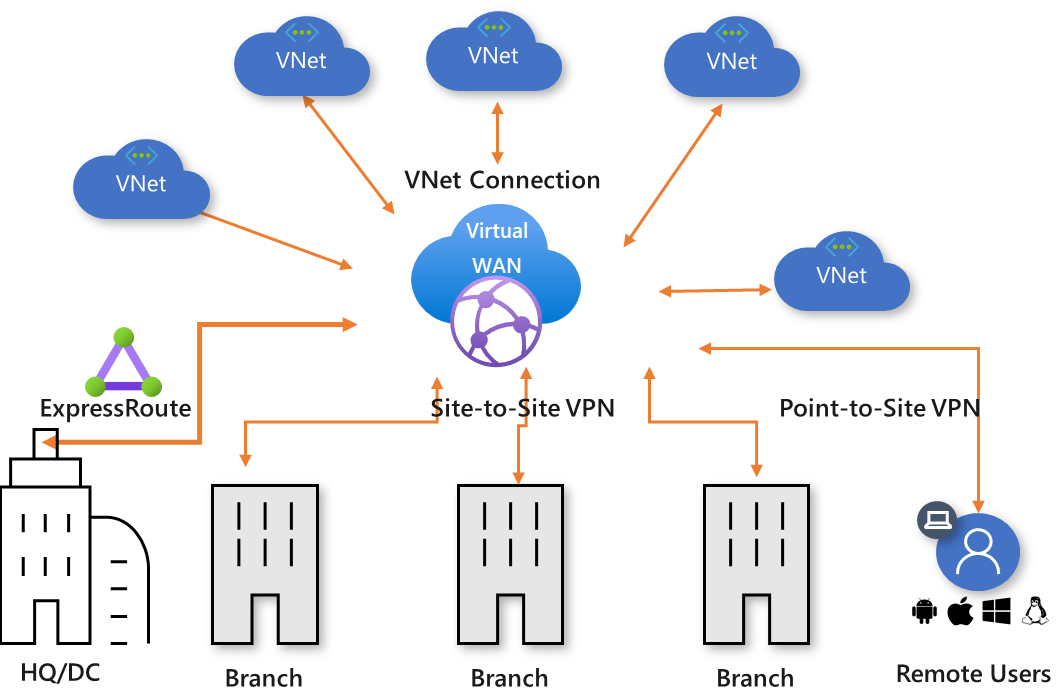
✅ Virtual Network Peering: Use VNet peering to connect VNets within the same region or across regions, allowing seamless resource access without performance bottlenecks.
✅ Azure Virtual WAN: Optimize and automate branch-to-branch connectivity with Azure Virtual WAN.
5️⃣ Monitor and Manage
✅ Azure Monitor: Use Azure Monitor to track the performance and health of your network resources. Set up alerts for critical events.
✅ Network Watcher: Utilize Network Watcher for network diagnostics and visualization. It helps in troubleshooting and monitoring network performance.
Best Practices?
Followings are the high-level “best practices” that will apply to most use cases:
✔️ Least Privilege Principle: Apply the principle of least privilege to all network resources.
✔️ Regular Audits: Conduct regular security audits and vulnerability assessments.
✔️ Automation: Use infrastructure as code (such as Bicep or ARM) to automate deployments and ensure consistency.
Reference architecture
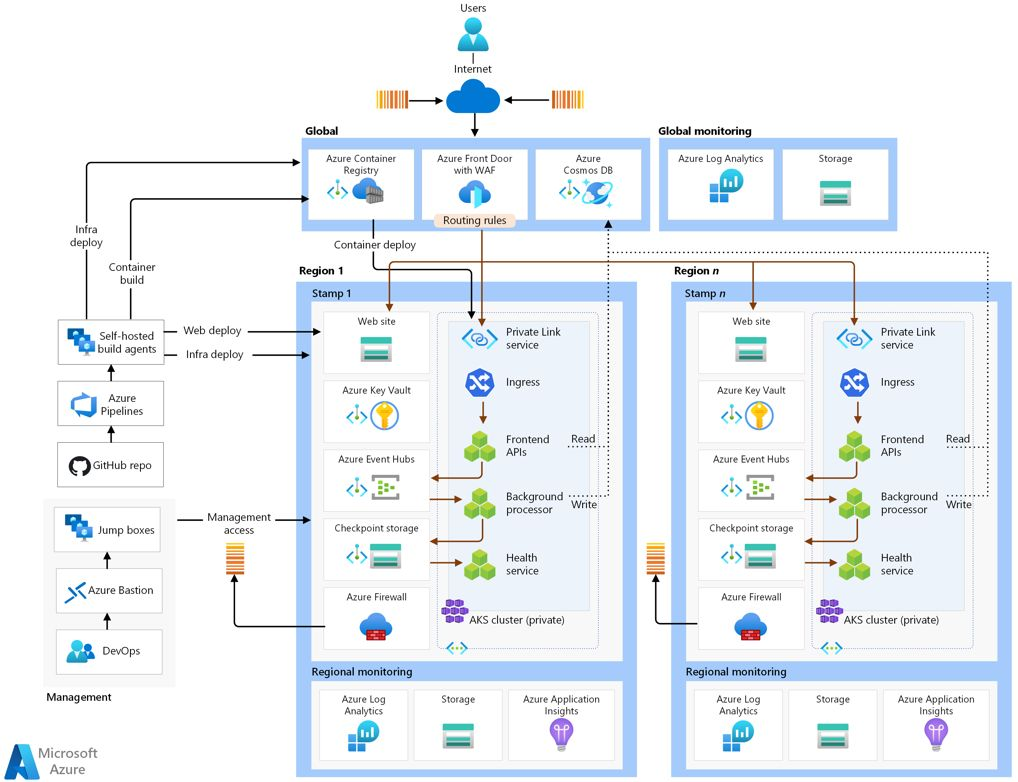
Following is a reference architecture from Microsoft learn documentation that aims to address the Mission-critical baseline architecture on Azure – and is focused on maximizing reliability and operational effectiveness.
Reference material URL 👉 https://learn.microsoft.com/azure/architecture/reference-architectures/containers/aks-mission-critical/mission-critical-intro?WT.mc_id=AZ-MVP-5004750
Call to action
Please, let me know your feedback and challenges with securing your Azure virtual networking environment.
You are always welcome to check my LinkedIn post and provide your valuable feedback 👉 https://www.linkedin.com/posts/elkhanyusubov_cloudmarathoner-microsoftazure-azurenetworking-activity-7282613021695197185-48hW