Hi Cloud Marathoners!
Welcome to the 10th blog post (Part 10/12) of the Azure Architect series to help you get ready for the AZ-305 exam. This post finalizes the third section of this exam – Design Data Storage Solutions.
Our next post will be discussing the last section of this exam – Design Business Continuity Solutions.
And please feel free to check the previous blog posts listed below if you landed on this page for the first time 🙂
Table of content (blog series)
- *** Design Identity, Governance, and Monitoring Solutions ***
- Part 1: Design a governance solution
- Part 2: Design Authentication and Authorization Solutions
- Part 3: Design a solution to log and monitor Azure resources
- *** Design Infrastructure Solutions ***
- Part 4: Design a compute solution
- Part 5: Design an application architecture solution
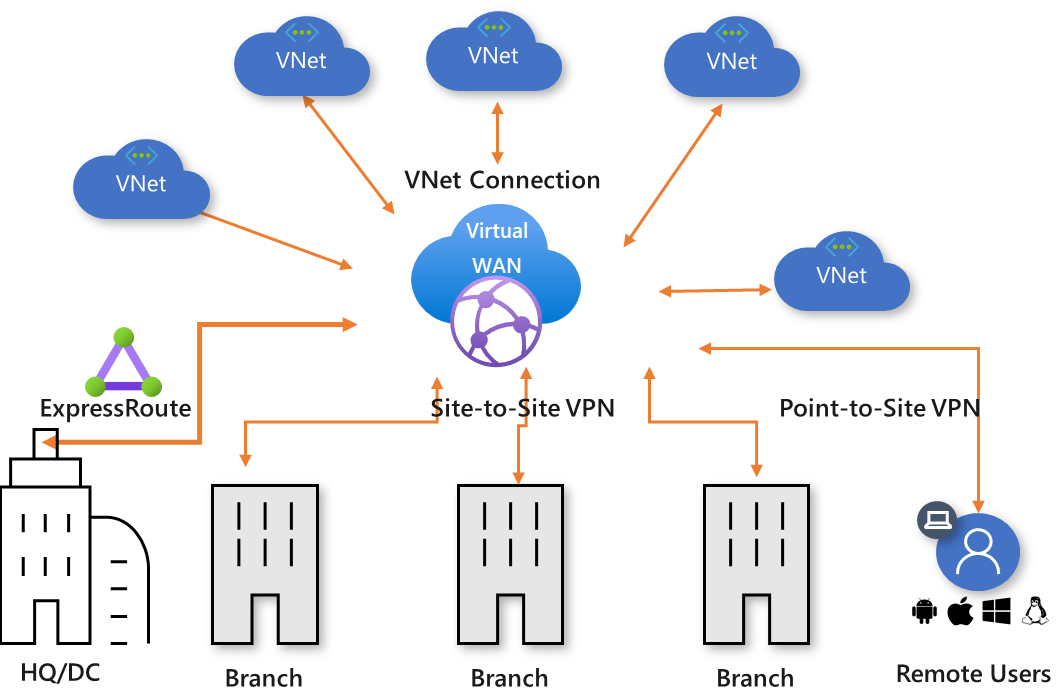
- Part 6: Design a network infrastructure solution
- Part 7: Design a migration solution
- *** Design Data Storage Solutions ****
- Part 8: Design a non-relational data storage solution
- Part 9: Design a data storage solution for relational data
- Part 10: Design a data integration solution
- *** Design Business Continuity Solutions ***
- Part 11: Design a solution for Business Continuity, backup and disaster recovery
- Part 12: Design for high availability
What is the Data Integration ?
It is very natural to wonder – “what is the meaning of data integration”?
In a nutshell, it is a combination of differently sourced data for a high-level overview and analysis. In other words, “Data Integration” – is a common term referring to the requirement to combine data from multiple separate business systems into a single unified view, also known as a single view of the truth.
This unified view is typically stored in a central data repository known as a data warehouse.
Data integration can serve your organization some short- and long-term benefits, including the followings:
✔️ Better Data
✔️ Better Collaboration
✔️ Fast connections between Data Storage
✔️ Increased efficiency and ROI
✔️ Better customer and partner experiences
✔️ A more comprehensive view of your business

What are the Data Integration solutions in Microsoft Azure?
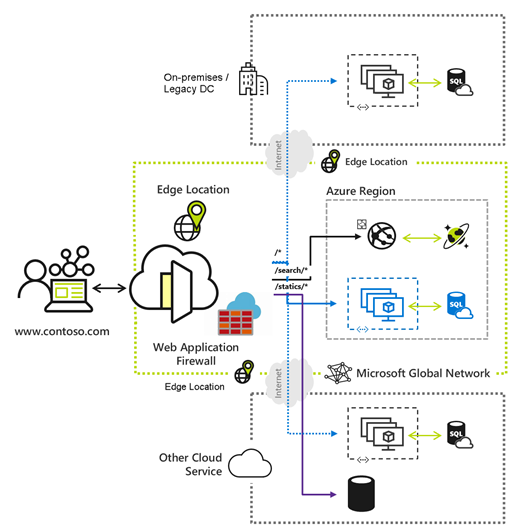
Application integration often requires connecting multiple independent systems, often in complex ways. This white paper explains how the components of Azure Integration Services—API Management, Logic Apps, Service Bus, and Event Grid—work together to provide a complete solution for integrating both cloud and on-premises applications.
Azure Integration Services
There are several Azure services such as Azure Functions, Azure Data Factory, and Azure Logic Apps are just a few of the services that can help you efficiently solve complex data challenges.

Check out the Overview of Data Integration in Azure from this official resource.
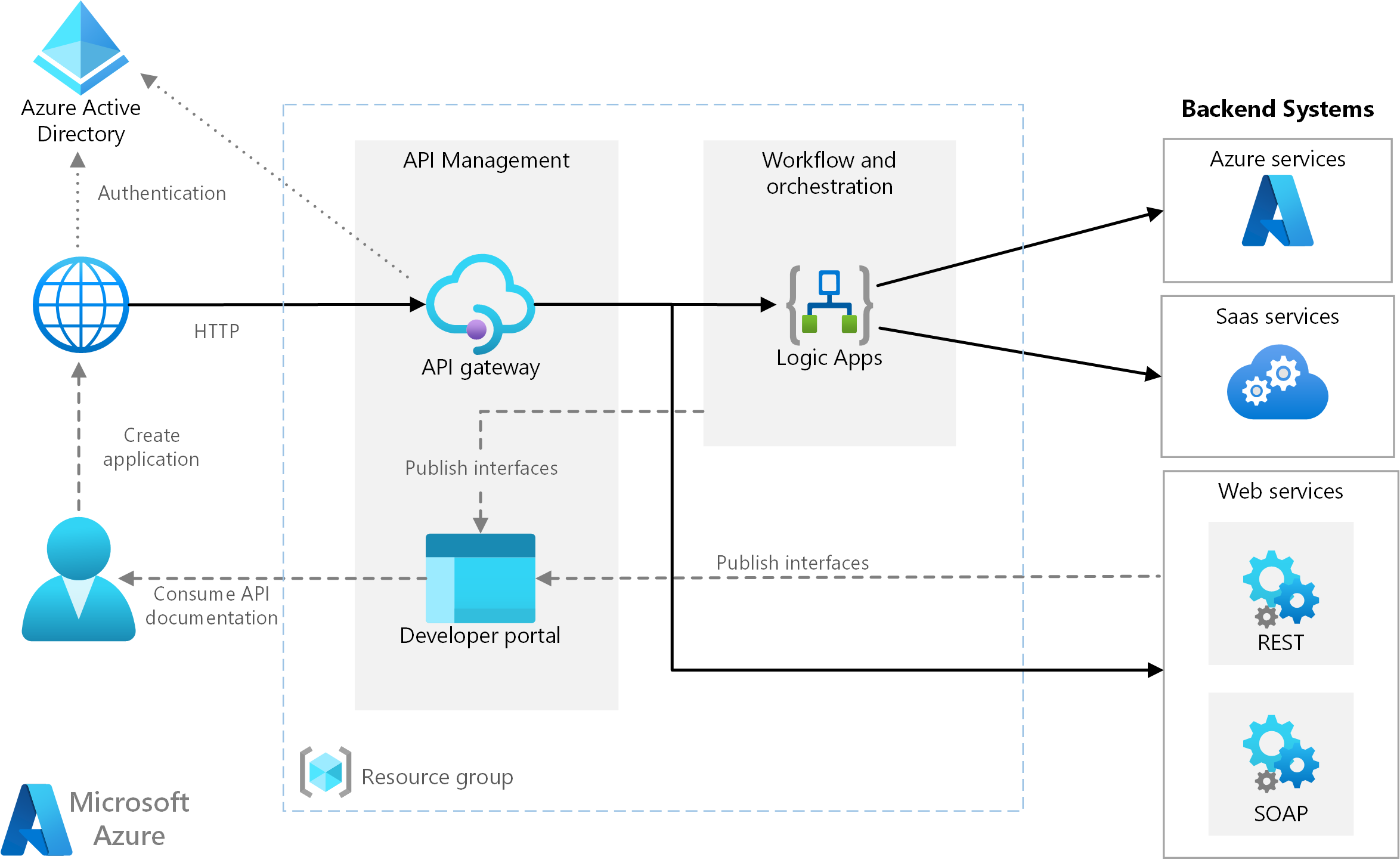
Part 10: Design a data integration solution
The references below are taken from official Microsoft docs and focused on designing Data Integration solutions in Azure. You could also find it helpful to check the Microsoft docs and learning paths with [Tutorials] below 😉.
This collection of links is gathered with a focus on the exam objectives of the AZ-305 certification exam.
What is Azure Logic Apps?
Azure Logic Apps documentation
What is Azure Service Bus?
Azure Service Bus Messaging documentation
[Tutorials] Azure Logic Apps on Microsoft Learn
[Tutorials] Azure Service Bus on Microsoft Learn
Introduction to Azure Functions
Azure Functions documentation
[Tutorials] Azure Functions on Microsoft Learn
About API Management
API Management documentation
[Tutorials] API Management on Microsoft learn
What is Azure Event Grid?
Azure Event Grid documentation
[Tutorials] Azure Event Grid on Microsoft Learn
Azure Data Factory
Azure Data Factory documentation
[Tutorials] Azure Data Factory on Microsoft Learn
Introduction to Azure Data Lake Storage Gen2
Overview of Azure Stream Analytics Cluster
Azure Stream Analytics documentation
Transact-SQL features supported in Azure Synapse SQL
Introducing data virtualization with PolyBase
Azure Data Lake
Analytics end-to-end with Azure Synapse
[Tutorial] Implement a Data Streaming Solution with Azure Streaming Analytics
Azure Synapse SQL architecture
What is Azure Synapse Analytics?
[Tutorial] Explore Azure database and analytics services
[Tutorial] Data integration at scale with Azure Data Factory or Azure Synapse Pipeline
What is Azure Databricks?
[Blog] 4 common analytics scenarios to build business agility
SUMMARY
Thank you for visiting the AZ-305 Study Guide and checking the Part 10: Design a data integration solution.
The next blog post will be continuation with Part 11: Design a business continuity solution.