Hi Cloud Marathoners!
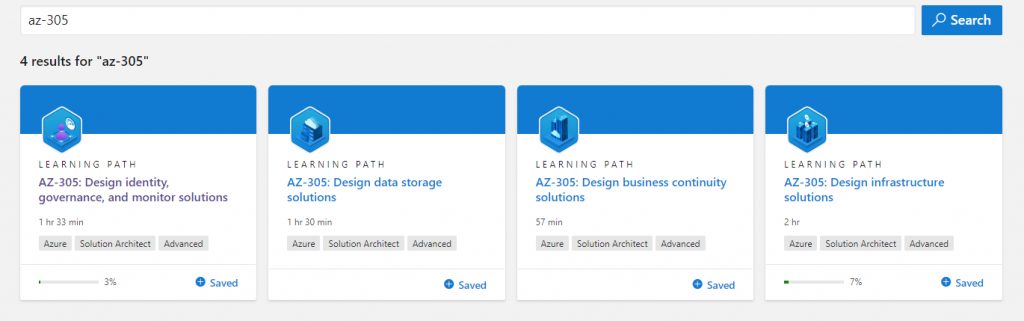
This is the continuation (Part 2/12) of blog post series to help you get ready for the latest AZ-305 exam. As title says – our focus will be on understanding and designing Authentication and Authorization Solutions in Microsoft Azure.
Feel free to check the previous post (Part 1/12) if you did not look into it yet 🙂
Table of content (blog series)
- *** Design Identity, Governance, and Monitoring Solutions ***
- Part 1: Design a governance solution
- Part 2: Design Authentication and Authorization Solutions
- Part 3: Design a solution to log and monitor Azure resources
- *** Design Infrastructure Solutions ***
- Part 4: Design a compute solution
- Part 5: Design an application architecture solution
- Part 6: Design a network infrastructure solution
- Part 7: Design a migration solution
- *** Design Data Storage Solutions ****
- Part 8: Design a non-relational data storage solution
- Part 9: Design a data storage solution for relational data
- Part 10: Design a data integration solution
- *** Design Business Continuity Solutions ***
- Part 11: Design a solution for Business Continuity, backup and disaster recovery
- Part 12: Design for high availability
What is the Authentication and Authorization?
To put it in plain English language, authentication is the process of verifying who someone is, where as authorization is the process of verifying what specific applications, files, and data a user has access to.
To relate these concepts to a real-world scenarious, you may think about your airport access and on-boarding to the plane experience. Thus, when you go through the security in an airport, you are required to show your ID to authenticate your identity. Then, you proceed and arrive at the gate, you present your boarding pass to the flight attendant, so they can authorize you to board your flight and allow access to your assigned seat.
WHAT YOU CAN DO WITH Authentication and Authorization?
The authentication and authorization services are part of the Microsoft’s identity platform.
The Authentication sometimes shortened to ‘AuthN’.
The Microsoft identity platform uses the OpenID Connect protocol for handling authentication. On the other hand, Authorization sometimes shortened to ‘AuthZ‘. The Microsoft identity platform uses the OAuth 2.0 protocol for handling authorization.
In Microsoft Azure your authentication and authorization is delegated to Azure Active Directory (Azure AD). By using this centralized identity provider you can enable following secure workflows for your business:
- Conditional Access policies – that require a user to be in a specific location.
- The use of multi-factor authentication, which is sometimes called two-factor authentication or 2FA.
- Enabling a user to sign in once and then be automatically signed in to all of the web apps that share the same centralized directory. This capability is called single sign-on (SSO).

Part 2: Designing Authentication and Authorization solutions
The references below are taken from official Microsoft docs and focused on designing Azure Authentication and Authorization solutions. You could also find it helpful to check the Microsoft docs and learning paths with [Tutorials] below 🙂
This collection of links is gathered with a focus on the exam objectives of the AZ-305 certification exam.
Azure identity management security overview
Azure Identity Management and access control security best practices
Five steps to securing your identity infrastructure
What is Azure Active Directory?
Compare Active Directory to Azure Active Directory
Azure Active Directory B2B best practices
Overview: Cross-tenant access with Azure AD External Identities (Preview)
Identity Providers for External Identities
Authentication and Conditional Access for External Identities
What is Azure Active Directory B2C?
Technical and feature overview of Azure Active Directory B2C
What is Conditional Access?
Plan a Conditional Access deployment
[Tutorial]: Secure user sign-in events with Azure AD Multi-Factor Authentication
[Tutorial]: Enable users to unlock their account or reset passwords using Azure AD self-service password reset (SSPR)
[Tutorial]: Enable Azure Active Directory self-service password reset writeback to an on-premises environment
What is Identity Protection?
What is risk?
Azure Active Directory Identity Protection – Security overview
Identity Protection policies
What are Azure AD access reviews?
What are managed identities for Azure resources?
What is identity lifecycle management?
Microsoft Azure Well-Architected Framework – Security
Authenticate apps to Azure services by using service principals and managed identities for Azure resources
Application and service principal objects in Azure AD
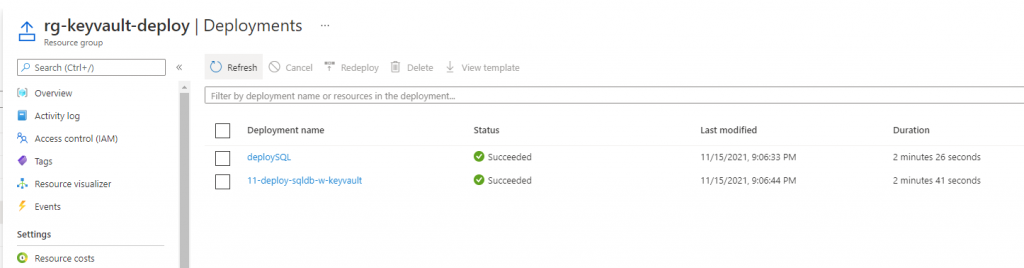
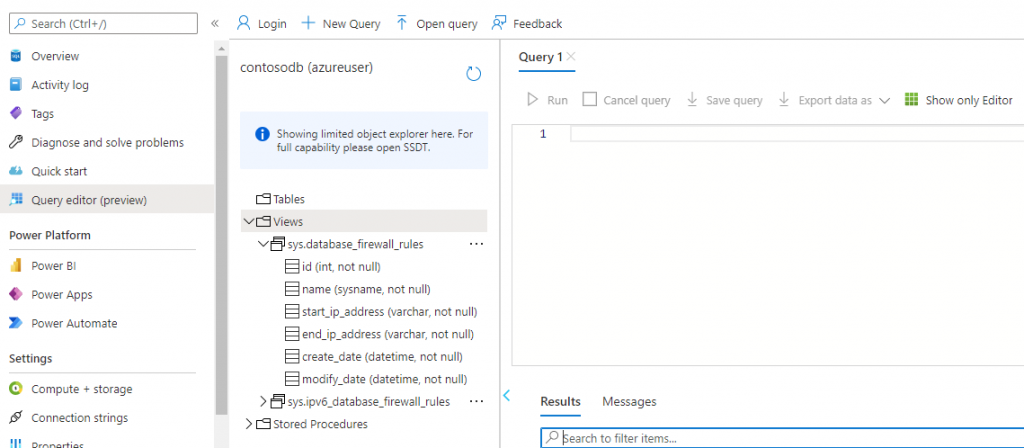
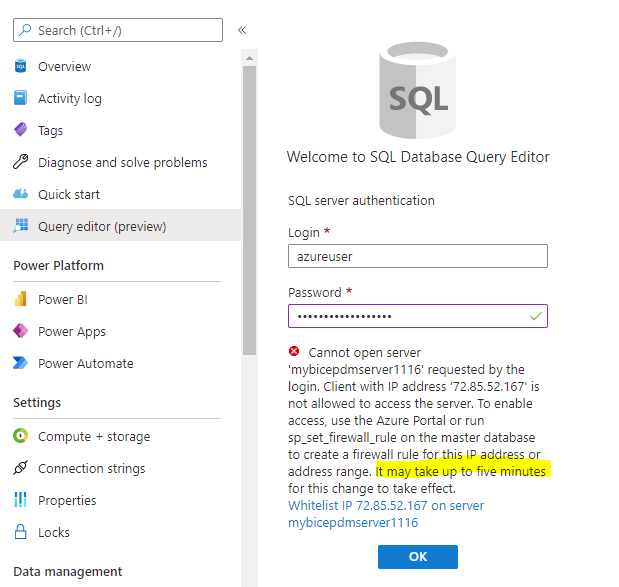
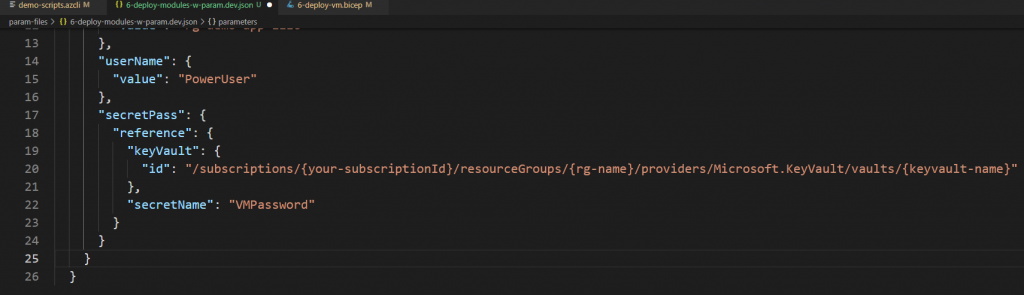
Azure Key Vault basic concepts
Best practices for using Azure Key Vault
Azure Key Vault logging
Virtual network service endpoints for Azure Key Vault
Monitoring Key Vault with Azure Event Grid
SUMMARY
Thank you for visiting the AZ-305 Study Guide and checking the Part 2 – Designing Authentication and Authorization Solutions.
The next blog will cover the Part 3: Design a solution to log and monitor Azure resources.