Hello cloud marathoners,
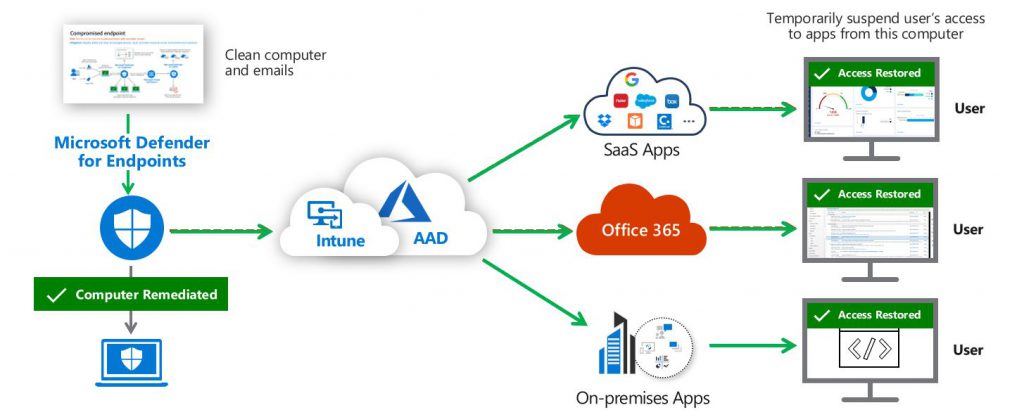
The MCAS (Microsoft Cloud App Security) 🛡️🔐 – helps to identify and combat cyberthreats across all your cloud services. This is a cloud access security broker (CASB) that provides multifunction visibility, control over data travel, and sophisticated analytics.
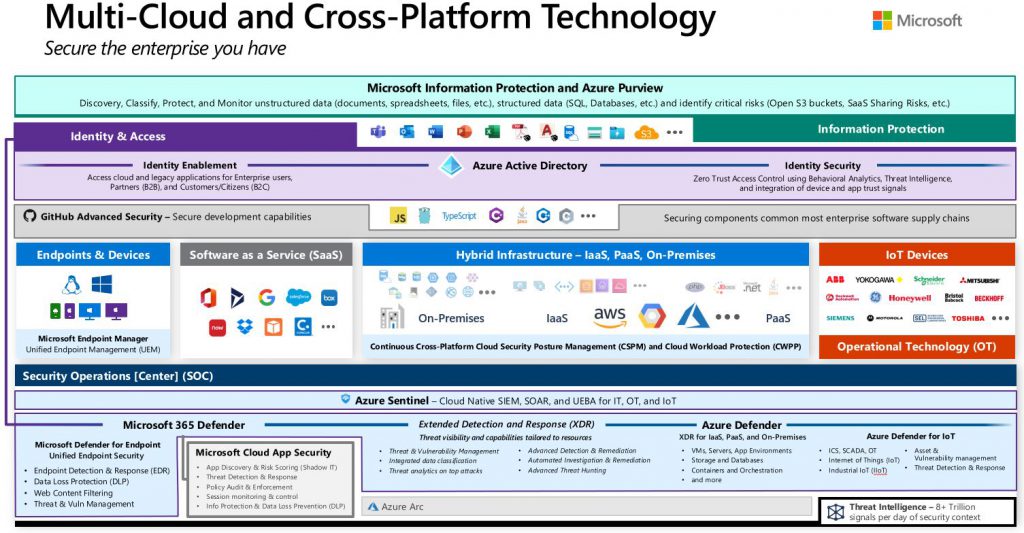
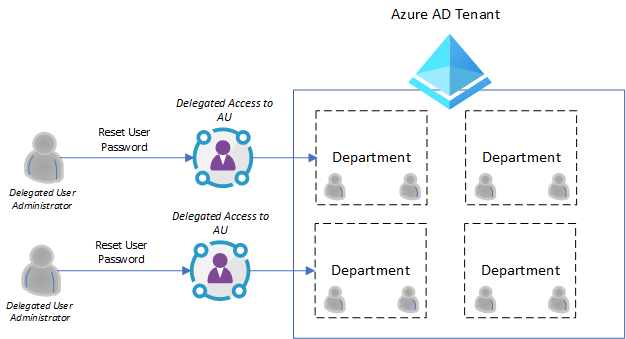
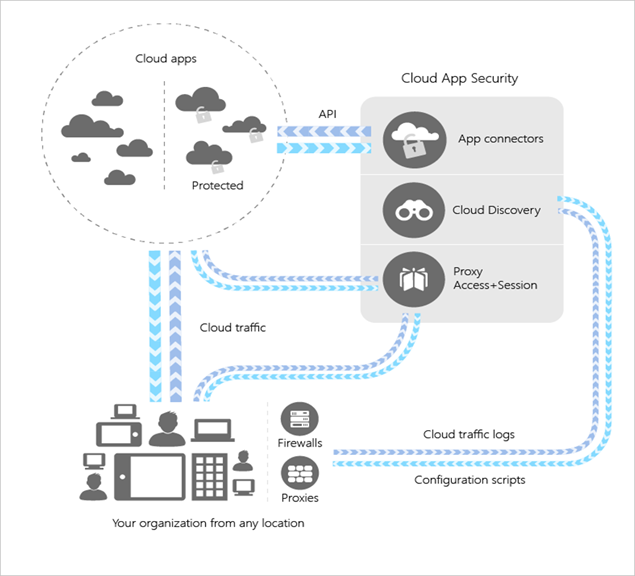
Here is a high level architecture diagram from Microsoft docs.
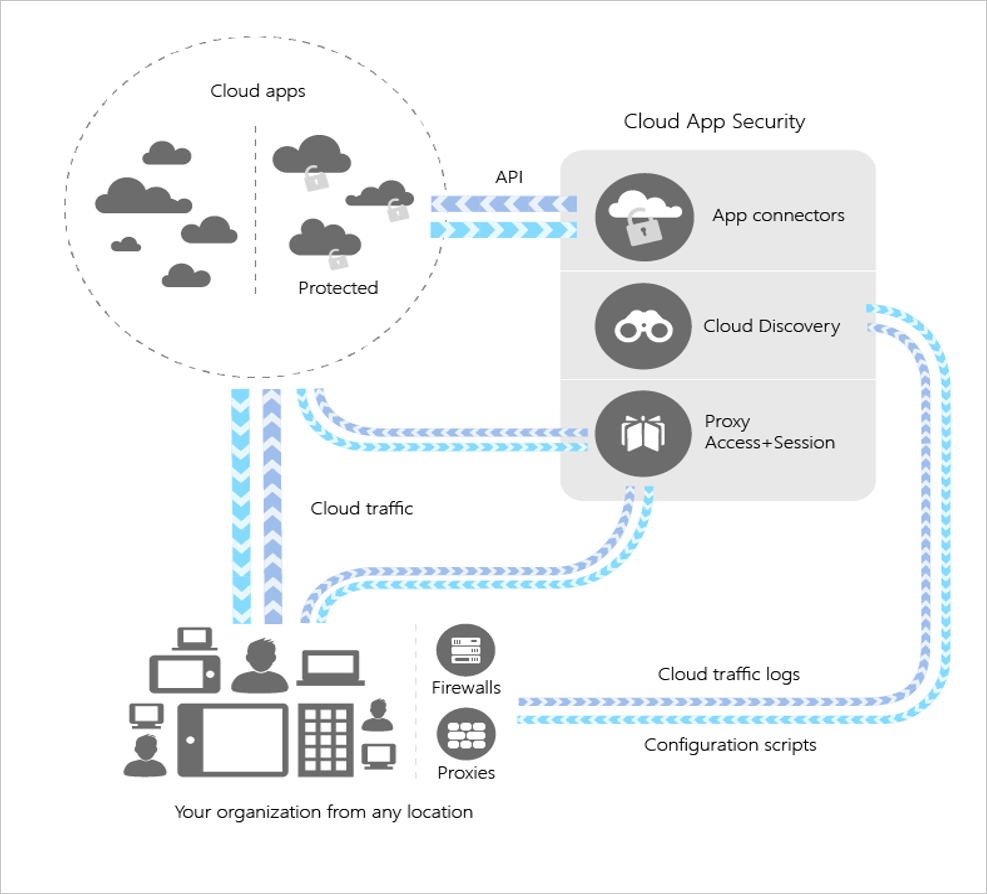
What are the main benefits of this cloud service?
Here are the main three benefits ot brings alone:
✔️ Discovery & Manage your apps
✔️ Govern access to apps and resources
✔️ Check compliance on your cloud apps
Check out this detailed level architecture of #appsecurity in Microsoft Azure ™ 👍
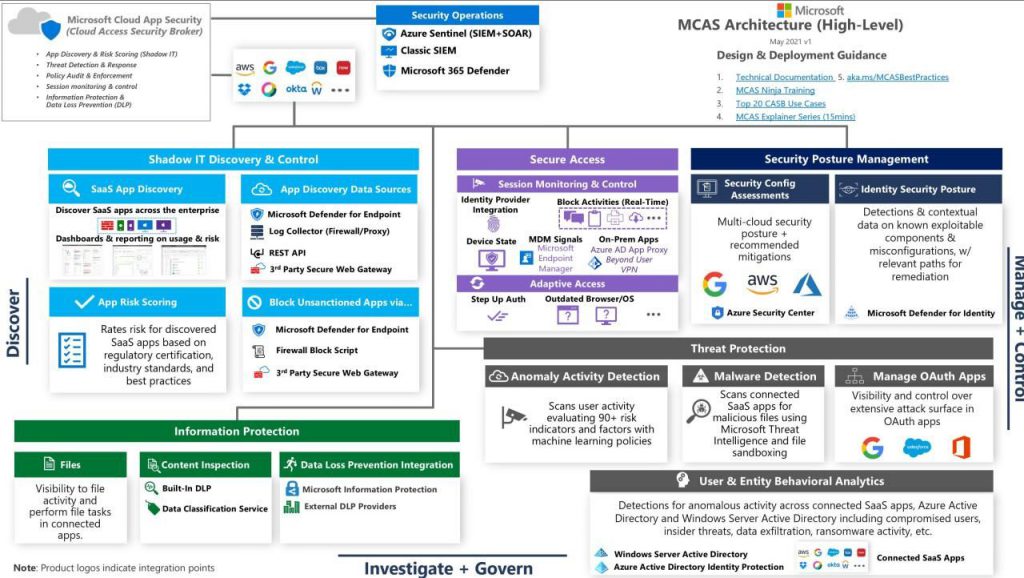
What are the main use cases for your business?
✔️ Shadow IT Discovery & Control
✔️ Secure Access
✔️ Security Poster Management
✔️ Threat Protection
✔️ Information Protection
✔️ User & Entity Behavioral Analytics
Another beauty of above architecture lies in a fact that you could easily integrate this model with third party SaaS apps, all listed on a diagram.
Thank you Matt Soseman for bringing this diagram #SharingIsCaring❤️️
Fᴏʟʟᴏᴡ ᴍᴇ 🎯 ᴀɴᴅ become ᴀ #cloudmarathoner ⛅🏃♂️🏃♀️ – 𝐋𝐄𝐓’𝐒 𝐂𝐎𝐍𝐍𝐄𝐂𝐓 👍
#microsoftazure
#MCAS#securitymanagement
#OAuth#secureaccess #appsec
#threatprotection
#securityengineering
#bestpractices
#continuouslearning